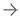Image courtesy of Carestream
According to the U.S. Department of Health and Human Services (HHS), about 70 percent of organizations are not compliant with the Health Insurance Portability and Accountability Act of 1996 (HIPAA). HIPAA mandates industry-wide standards for healthcare information and electronic billing, and requires protection as well as confidential handling of protected health information.
According to HIPAA rules, any company that deals with protected information must have a physical network and process security measures that are followed to ensure compliance. It may be safe to say that many organizations are still perplexed about HIPAA audits, enforcements and compliance. As a result, the number of organizations that fail to meet compliance each year remain the majority.
To begin understanding compliance, healthcare organizations would be wise to consider three key recommendations.
1. Analyze the Past to Avoid Making the Same Mistake Twice
It is important for hospitals and healthcare facilities to look at some of the common mistakes that are repeatedly noted in HIPAA security reviews. HIPAA states that out of all the reviews completed, there are a number of frequent compliance violations and issues that are found each year. This includes:
• Impermissible uses and disclosures of protected health information;
• Lack of safeguards to protect health information;
• Lack of patient access to their personal health information;
• Lack of administrative safeguards on electronic protected health information; and
• Use or disclosure of more than the minimum protected health information.
Protecting valuable data by analyzing past mistakes is an important step in the compliance process.
2. Perform a Risk Assessment and Gap Analysis
One preventive measure in assessing an organization’s compliance with HIPAA is a risk analysis and a gap analysis. The confusion and lack of understanding around the two examinations has been common among healthcare professionals in the marketplace for some time. Not understanding the differences can be detrimental to an organization and puts it at a significantly higher risk. According to HHS and Office for Civil Rights (OCR) guidelines, all healthcare organizations must specifically conduct a risk analysis to be deemed within HIPAA compliance.
A HIPAA gap analysis can be used to measure the organization’s information security standing against HIPAA, which is part of HHS audit protocol. Comparing the organization’s current practices to the HHS OCR audit protocol will identify the strengths and weaknesses of the security program. From there, the organization can determine whether they have reasonable and appropriate administrative, physical and technical safeguards in place to protect patient health records. Performance of the gap analysis also allows the organization to develop an audit response toolkit that includes the data and documentation that would be able to support compliance with the HIPAA regulations to regulatory agencies.
The risk analysis is a required control as defined in audit protocol. Without conducting a thorough and comprehensive risk analysis, a healthcare organization cannot identify applicable threats and vulnerabilities that allow for them to take corrective action. Completing a thorough risk analysis provides insight into the organization’s security position and allows for change before an audit takes place. Risk analyses should also be updated at least annually to ensure they reflect current operational practices.
To begin, an organization should document any electronic personal health information (ePHI) transmitting or processing services. This includes any business associates or employees that receive and use the ePHI. It is important to evaluate all aspects of the organization’s operation to verify all uses and disclosures of ePHI are identified. Do not assume that your IT shop is aware of all of your uses and disclosures, inquire of all of the operational areas of your organization.
The risk assessment should evaluate the security, use and disclosure of PHI against HIPAA’s privacy, security and breach notification implementation specifications.
3. Develop an Action Plan and a Response Toolkit
For many healthcare organizations, the question is not if they will receive a HIPAA audit or an OCR investigation, but when. The OCR, which is responsible for completing HIPAA audits, will contact the organization. The OCR will further ask for a variety of documents and data. Once these documents and data are reviewed, the OCR will send the organization a preliminary copy of its findings. This preliminary report gives healthcare organizations the opportunity to respond to the OCR, and have its responses included in the final report.
From the final report, the OCR will determine if an organization was in compliance of HIPAA and, if not, where an organization was lacking. If an organization was not in total compliance, the OCR will provide corrective action and technical assistance the organization can use to work toward compliance.
Developing an action plan and evaluating the organization’s information security against the OCR audit protocol to develop an audit response toolkit will leave organizations with practical actions that serve their best interest, eliminate mistakes and mitigate risk.
Carol Amick is an experienced healthcare compliance professional with over 20 years of experience in healthcare. After starting her career at HCA she moved on to become a compliance consultant for a “Big 4” accounting firm, and has since served as the internal audit director, compliance director and privacy officer for several healthcare providers. Amick has worked with post-acute care, outpatient, and acute care providers to develop and implement effective compliance programs. During her time as compliance and privacy director, she led numerous investigations into PHI breaches and responded to outside investigations by the OCR, OIG and other regulatory agencies. She currently serves as the manager of healthcare services at CompliancePoint.



 July 30, 2024
July 30, 2024