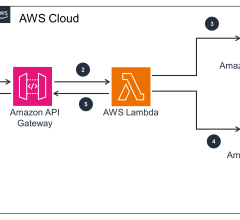
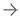April 15, 2020 — Frost & Sullivan’s recent analysis, The Future of Privacy and Cybersecurity, Forecast to 2030, finds that by 2030, there will be a complex global network of 200 billion devices, with over 20 connected devices per human. As the Internet of Things landscape is expected to progressively expand beyond the traditional network in use today, there will be an increase in the complexity of privacy and cybersecurity challenges. Consequently, the market will experience deeper synergies among data protection, security, privacy, and public good as more international frameworks are developed to govern the internet.
"Artificial Intelligence (AI) will emerge as the new frontier of privacy and cybersecurity as enterprises explore new opportunities and train a capable workforce to identify critical threats, respond faster to breaches, and learn from them,” said Vinay Venkatesan, Visionary Innovation Research Consultant. "In addition to AI, data de-identification, advanced authentication and encryption, biometrics, Blockchain, automation, and quantum computing also will have the potential to transform privacy and cybersecurity."
Venkatesan added: "There will be more than 26 smart cities by 2025, most of them in North America and Europe. Additionally, boundaries between work and home continue to blur, as we’re experiencing right now. This means every connected device in a smart home, enterprise or city will be a potential access point to our most sensitive and personal data, making mass non-consensual data collection feasible and cybersecurity all the more vital."
For further revenue opportunities, cybersecurity vendors should:
- Invest in/partner with startups offering technological innovations (Blockchain, AI) at the core.
- Adopt an enterprise-wide cyber defense strategy rather than a dedicated cybersecurity unit.
- Invest in a creative, “cyber-human” workforce with the flexibility to deal with the evolving nature of threats.
- Allocate dedicated budgets for post-breach response solutions and recovery mechanisms.
- Consider integrating solutions offering end-to-end security built into the system rather than “bolt-on” security features.
For more information: ww2.frost.com/research/visionary-innovation/

 August 29, 2024
August 29, 2024